



The problem of insecure software is perhaps the most important technical challenge of our time. The dramatic rise of web applications and mobile applications enabling business, social networking etc has only compounded the requirements to establish a robust approach to writing and securing our Internet, Web Applications and Data
We at Security Testing Centre of Excellence, our focus is to serve our clients as trusted advisors by securing their information and operational IT assets. Our approach is based on experience and expertise of real world business problems and delivery of pragmatic, appropriate and cost effective solutions. Our commitment to our customers is better represented by our caption, “YOU FOCUS ON YOUR CORE BUSINESS, WE WILL TAKE CARE OF THE IT SECURITY”.
Security Testing is carried out to ensure appropriate secure access to each User group and to restrict access to any malicious attacks. Secure Access ensures the following parameters
 Penetration Testing will revel real world opportunities for intruders to compromise systems and networks in such a way that allows for unauthorized access to sensitive data or even take over systems for malicious or non-business purposes. Network penetration test sub categorized as Internal Penetration Test & External Penetration Test.
Penetration Testing will revel real world opportunities for intruders to compromise systems and networks in such a way that allows for unauthorized access to sensitive data or even take over systems for malicious or non-business purposes. Network penetration test sub categorized as Internal Penetration Test & External Penetration Test.
 Websites are a huge part of the web and plays vital role in offering many Information. We carry over years of experience in the information security domain and have flawlessly executed website security testing assignments against 1000+ websites in the past, which helps us derive the right solutions for the businesses to safeguard its public websites.
Websites are a huge part of the web and plays vital role in offering many Information. We carry over years of experience in the information security domain and have flawlessly executed website security testing assignments against 1000+ websites in the past, which helps us derive the right solutions for the businesses to safeguard its public websites.
 Mobile usages are increasing day by day, over the last few years, smart phones and tablets have become main stream in both, consumer and enterprise markets. Keeping information secure on mobile devices is crucial for companies and end users, be it corporate or personal. One of the consistent method to ensure the security is performing an end-to-end mobile app penetration test. Emulator and real device security test is mandatory as part of mobile app penetration test.
Mobile usages are increasing day by day, over the last few years, smart phones and tablets have become main stream in both, consumer and enterprise markets. Keeping information secure on mobile devices is crucial for companies and end users, be it corporate or personal. One of the consistent method to ensure the security is performing an end-to-end mobile app penetration test. Emulator and real device security test is mandatory as part of mobile app penetration test.
![]() Database servers often hold your organization’s most sensitive and valuable information. some times with default passwords and unencrypted data, providing attackers with an open back door. Insiders can steal company secrets, intellectual property or card details right off your network, making it critical to test the security of your databases from Inside the organization. By engaging skilled testers, you can ensure that new vulnerabilities are exposed and fixed, before Hackers exploit them.
Database servers often hold your organization’s most sensitive and valuable information. some times with default passwords and unencrypted data, providing attackers with an open back door. Insiders can steal company secrets, intellectual property or card details right off your network, making it critical to test the security of your databases from Inside the organization. By engaging skilled testers, you can ensure that new vulnerabilities are exposed and fixed, before Hackers exploit them.
![]() SAP Vulnerability Assessment services can be utilized to identify critical vulnerabilities affecting your current SAP Platform and application layer. SAP Penetration testing is to detect issues in the technical protection of existing SAP Systems at the following levels: Operating system, database and network access. In particular, it analyses whether third parties without user Ids can log on to the system and whether internal users that have user IDs with low authorization can enhance their privileges.
SAP Vulnerability Assessment services can be utilized to identify critical vulnerabilities affecting your current SAP Platform and application layer. SAP Penetration testing is to detect issues in the technical protection of existing SAP Systems at the following levels: Operating system, database and network access. In particular, it analyses whether third parties without user Ids can log on to the system and whether internal users that have user IDs with low authorization can enhance their privileges.
 Citrix Remote Access Penetration test verifies whether entry points to your internal infrastructure are properly secured. Testing typically Involves Citrix, VPN, PPTP and Dial-In links. Remote Access infrastructure test generally simulate an authenticated external user attempting to compromise the infrastructure through remote access channel. Citrix environments with any number of misconfigurations that would allow an attacker or malicious user to compromise the system break out of a restricted environment, steal data or income cases, to compromise internal networks from the Internet.
Citrix Remote Access Penetration test verifies whether entry points to your internal infrastructure are properly secured. Testing typically Involves Citrix, VPN, PPTP and Dial-In links. Remote Access infrastructure test generally simulate an authenticated external user attempting to compromise the infrastructure through remote access channel. Citrix environments with any number of misconfigurations that would allow an attacker or malicious user to compromise the system break out of a restricted environment, steal data or income cases, to compromise internal networks from the Internet.
![]() VoIP penetration testing includes assessing the VoIP infrastructure and
VoIP penetration testing includes assessing the VoIP infrastructure and
Determining the risks of a classic internal network infrastructure attack. We evaluate the different VoIP components from a security perspective and their capability to maintain the confidentiality, integrity and availability of the environment and related traffic. Our testing generally includes investigating the authentication mechanisms as well as the potential interception, interruption or manipulation of the exchanged information between the client and VoIP server.
 Wireless Security Assessment is a combination of a Wireless Penetration Test and a Vulnerability Assessment. Brisk InfoSec’s wireless penetration testing and assessment services help businesses evaluate the security of their wireless communication and provide recommendations for improvement. We are supporting various wireless technology such as for WIFI, Bluetooth, Zigbee etc.
Wireless Security Assessment is a combination of a Wireless Penetration Test and a Vulnerability Assessment. Brisk InfoSec’s wireless penetration testing and assessment services help businesses evaluate the security of their wireless communication and provide recommendations for improvement. We are supporting various wireless technology such as for WIFI, Bluetooth, Zigbee etc.
![]() Internet of Things (IoT) security requires a combination of embedded
Internet of Things (IoT) security requires a combination of embedded
software, data, mobile application and cloud security. Testing Software and systems for IoT also involves physical, sensory and emotional interactions. Because today’s digital devices not only work based on keystrokes but also respond to our touch, motion and voice. Testing IoT also will need to involve testing all possible devices for all possible permutations and combinations of Operating Systems and Software supported.
 VPN Penetration testing is done to discover any vulnerabilities in the VPN implementation that an attacker may exploit. This is usually considered as zero knowledge test where only the IP address of the VPN server is known. We Start off by determining the type of VPN implementation in an organization which might include IPsec, PPTP or SSL based VPN capabilities. We will test authentication, authorization levels and split tunneling etc.
VPN Penetration testing is done to discover any vulnerabilities in the VPN implementation that an attacker may exploit. This is usually considered as zero knowledge test where only the IP address of the VPN server is known. We Start off by determining the type of VPN implementation in an organization which might include IPsec, PPTP or SSL based VPN capabilities. We will test authentication, authorization levels and split tunneling etc.
 > We review the complete IT infrastructure, Networking, Business Applications, Data Security and controls
> We review the complete IT infrastructure, Networking, Business Applications, Data Security and controls
> Alignment of IS strategy to business strategy enabling companies to invest in proper IS Assets Helping in quantifying the value of IS, particularly during acquisitions or disposals
 During source code reviews of web applications, web-specific vulnerabilities such as Cross-Site Scripting, SQL Injection, Cross-Site Request Forgery, Arbitrary Code Injection and XML Injection are detected. All possible aspects of application security are tested, including:
During source code reviews of web applications, web-specific vulnerabilities such as Cross-Site Scripting, SQL Injection, Cross-Site Request Forgery, Arbitrary Code Injection and XML Injection are detected. All possible aspects of application security are tested, including:
> Insufficient filtration of user-supplied data
> Improper memory management and buffer boundary checks
> Application logic flaws and race conditions
> Authentication and authorization bypass > Usage of unsafe methods and functions
> Sensitive information disclosure
 Health Insurance Portability and Accountability Act (HIPAA), Compliance regulations, define requirements to continuously secure electronic protected health information (EPHI), as it travels the healthcare systems in USA. We offer HIPAA Compliance service which enforces administrative procedures, technical security mechanisms, services, physical safeguards, by ensuring HIPPA Compliance and Assessment along with clear cut penetration test. We also guide and assist Healthcare entities, providers, payers and clearing houses for EPHI.
Health Insurance Portability and Accountability Act (HIPAA), Compliance regulations, define requirements to continuously secure electronic protected health information (EPHI), as it travels the healthcare systems in USA. We offer HIPAA Compliance service which enforces administrative procedures, technical security mechanisms, services, physical safeguards, by ensuring HIPPA Compliance and Assessment along with clear cut penetration test. We also guide and assist Healthcare entities, providers, payers and clearing houses for EPHI.
Novature Tech follows on demand Security Test frameworks to audit and discover internal & external vulnerabilities/weaknesses in the target application and hosts. The audit are carried out based on International Industry Standards such as
Novature Tech Penetration Test Process Typical phases of the application penetration testing are depicted in the figure below:
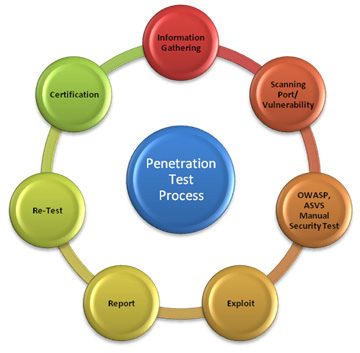
Information Gathering is performing reconnaissance against a target to gather as much information as possible to be utilized when penetrating the target during the vulnerability assessment and exploitation phases. The more information you are able to gather during this phase, the more vectors of attack you may be able to use in the future.
Open source intelligence (OSINT) is a form of intelligence collection management that involves finding, selecting, and acquiring information from publicly available sources and analysing it to produce actionable intelligence.
A commercial / Open source security scanner, used to identify security vulnerabilities and open ports in each user categories with and without logins to identify all well-known vulnerabilities with application.
Security testers follow OWASP ASVS manual security checklist and do the test using Burp Suite Pro manual intercept proxy to identify most common/ hidden vulnerability with the application.
The exploitation phase of a penetration test focuses solely on establishing access to a system or resource by bypassing security restrictions. The main focus is to identify the main entry point into the organization and to identify high value target assets. If the vulnerability analysis phase was properly completed, a high value target list should have been complied. Ultimately the attack vector should take into consideration the success probability and highest impact on the organization.
This document is intended to define the base criteria for penetration testing reporting. This report will give proof to developers and will guide them to identify the right fix for each vulnerability.
Retest activity is carried out after fixing reported vulnerability in earlier penetration test report. This ensures the appropriate level of security controls in application.
Once the Security Testing is completed with no outstanding Critical and High Security Threats, Security Test Consultant would release the Certificate.
Each assessment tool has the same basic concept – scan hosts attached to a network and run a series of tests in an effort to determine which host is vulnerable to a known catalogue of vulnerabilities. Vulnerability assessment tools differ themselves from others by speed, feature and cost. Of all the vulnerability assessments tools available today, each provides functionality resulting in a more complete asset inspection and asset definition. Whether vulnerability assessment software is device based, runs from a single node or is multi-perspective, the goal is to assess and report vulnerability. Also the tool uses the mechanisms to reduce the data into a smaller defined scope thus providing greater preventability. Below are some of the tools that our consultant uses for Security Testing. Our Security Consultant may use other tools not listed here as well if required.
© 2024 Novature Tech Pvt Ltd. All Rights Reserved.