




SECURITY TESTING
The software application can be secured by performing Security Testing. Security Testing is a type of Software Testing that uncovers vulnerabilities, threats, and risks in a software application and prevents malicious attacks from intruders. Security testing of any system is focuses on finding all possible loopholes and weaknesses of the system which might result into the loss of information or repute of the organization.
WHY SOFTWARE SECURITY TESTING
Security testing is very much important for software application as it takes care of confidential data. It ensures that confidential data does not get overlooked by an unauthorized entity. It works beyond functional (i.e. black box) and implementation (i.e. white box) testing. Security testers may use many techniques to locate system vulnerabilities. Testing a systems security checks the loopholes or vulnerabilities in the system which may cause failure of security functions of the system ultimately leading to great losses to the organization. Therefore, security testing is employed to ensure that developed software is free from flaws and hence, the system is safe from an unauthorized individual, be it an employee or an outsider. Security testing identifies threats and measures their impact on the system. The impact is analyzed by developers or testers by playing the role of an attacker. They put their efforts to break the system or getting into it to find bugs. So, security testing is very essential in IT sector for data protection
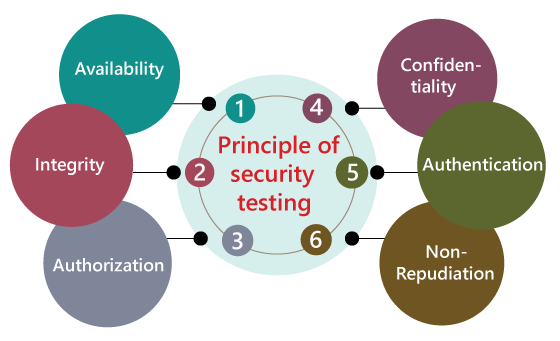
PRINCIPLES OF SECURITY TESTING
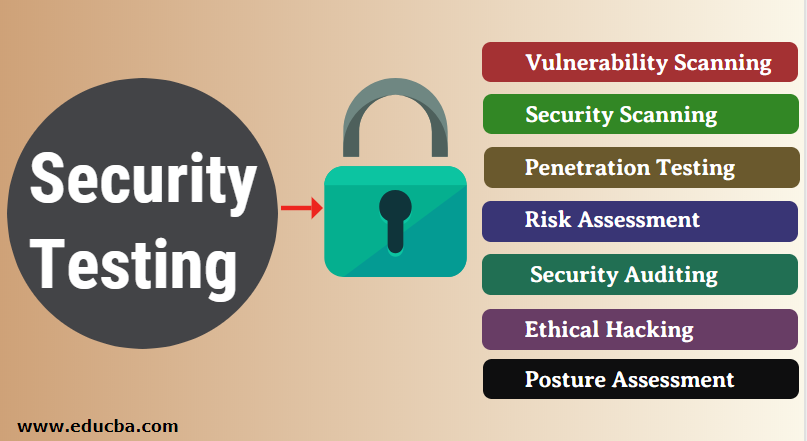
TYPES OF SECURITY TESTING
There are 7 types of security testing in software testing. These are as follows:
Vulnerability scanning: An automated software scans a system against identified vulnerability.
Security scanning: This scanning can be performed for both Manual and Automated scanning. It identifies the network and system weaknesses. After that, it provides the solution as well
Penetration testing: An analysis of a system to check for the potential vulnerabilities, if there is an external hacking attempt.
Risk assessment: The analysis of security risks observed in the organization is done here. Risks are classified as Low, Medium and High. It helps to provide measures in order to reduce the risks.
Security auditing: It’s a kind of internal inspection of applications and Operating systems for checking the security flaws.
Posture assessment: This combines security scanning, ethical hacking and risk assessments to represent overall security of the organization.
Ethical hacking: The hackers attempt hacking in order to expose the flaws in the security system of the organization.
HOW TO TEST APPILICATION SECURITY – WEB AND DESKTOP APPILICATION SECURITY TESTING TECHNIQUES
Need for Security Testing
The software industry has achieved solid recognition in this age. In recent decades, however, the cyber-world seems to be an even more dominating and driving force which is shaping up the new forms of almost every business.
Web-based ERP systems used today are the best evidence that IT has revolutionized our beloved global village. These days, websites are not only meant for publicity or marketing but they have evolved into stronger tools to cater to complete business needs.
Desktop And Web Security Testing
A desktop application should be secure not only regarding its access but also with respect to the organization and storage of its data.
Similarly, web applications demand, even more, security with respect to their access, along with data protection. A web developer should make the application immune to SQL Injections, Brute Force Attacks, and XSS (cross-site scripting). Similarly, if the web application facilitates remote access points then these must be secure too.
SECURITY TESTING TECHNIQUES
Access to Application
Whether it is a desktop application or a website, access security is implemented by “Roles and Rights Management”. It is often done implicitly while covering functionality.
How to Test: In order to test this, thorough testing of all roles and rights should be performed.
The tester should create several user accounts with different as well as multiple roles. He should then be able to use the application with the help of these accounts and should verify that every role has access to its own modules, screens, forms, and menus only. If the tester finds any conflict, then he should log a security issue with complete confidence
So, basically, you need to test who you are and what you can do for distinct users.
Some of the authentication tests include a test for password quality rules, a test for default logins, a test for password recovery, a test captcha, a test for logout functionality, a test for password change, a test for security question/answer, etc.
Similarly, some of the authorization tests include a test for path traversal, test for missing authorization, test for horizontal access control problems.
Data Protection
Test Data Protection: The tester should query the database for passwords of the user account, billing information of clients, and other business-critical and sensitive data, and should verify that all such data is saved in encrypted form in the DB.
Similarly, he must verify that the data is transmitted between different forms or screens after proper encryption only. Moreover, the tester should ensure that the encrypted data is properly decrypted at the destination. Special attention should be paid to different ‘submit’ actions.
The tester must verify that when the information is being transmitted between the client and server, it is not displayed in the address bar of a web browser in an understandable format. If any of these verifications fail, then the application definitely has a security flaw.
The tester should also check for proper use of salting (appending an extra secret value to the end input like password and thus making it stronger and more difficult to be cracked)
Brute-Force Attack
Test Brute-Force Attack: The tester must verify that some mechanism of account suspension is available and is working accurately. He must attempt to login with invalid user IDs and Passwords alternatively to make sure that the software application blocks the account if continuous attempts are made to login with invalid credentials.
If the application is doing so, then it is secure against brute-force attacks. Otherwise, this security vulnerability must be reported by the tester.
Testing for brute force can also be divided into two parts – black box testing and grey-box testing.
In Black box testing, the authentication method employed by the application is discovered and tested. Furthermore, the grey box testing is based on partial knowledge of password & account details and memory trade-off attacks.
SQL Injection And XSS
Test SQL Injection And XSS: The tester must ensure that maximum lengths of all input fields are defined and implemented. (S)He should also ensure that the defined length of input fields does not accommodate any script input as well as tag input. Both of these can be easily tested.
It should also be verified by the tester that the application does not support anonymous access methods. If any of these vulnerabilities exist, then the application is in danger
Service Access Points
Test Service Access Points: Let me explain it with the example of the stock trading web application; an investor (who wants to purchase the shares) should have access to current and historical data on stock prices. The user should be given the facility to download this historical data. This demands that the application should be open enough.
By accommodating and secure, I mean that the application should facilitate investors to trade freely (under the legislative regulations). They may purchase or sell 24/7 and the data of transactions must be immune to any hacking attack.
Moreover, a large number of users will be interacting with the application simultaneously, so the application should provide enough access points to entertain all the users.
In some cases, these access points can be sealed for unwanted applications or people. This depends on the business domain of the application and its users.
Session Management
A web session is a sequence of HTTP requests and response transactions linked to the same user. Session management tests check how session management is handled in the web app.
You can test for session expiry after a particular idle time, session termination after maximum lifetime, session termination after log out, check for session cookie scope and duration, test if a single user can have multiple simultaneous sessions
Error handling
Testing for Error handling includes:
Check for error codes: For example, test 408 request time-out, 400 bad requests, 404 not found, etc. To test this, you need to make certain requests on the page such that these error codes are returned.
The error code will be returned with a detailed message. This message should not contain any critical information that can be used for hacking purposes
Check for stack traces: It basically includes giving some exceptional input to the application such that the returned error message contains stack traces that have interesting information for hackers.
Specific Risky Functionalities
Mainly, the two risky functionalities are payments and file uploads. These functionalities should be tested very well. For file uploads, you need to primarily test if any unwanted or malicious file upload is restricted.
For payments, you need to primarily test for injection vulnerabilities, insecure cryptographic storage, buffer overflows, password guessing
Author: Arul Selvar | Posted On: 12th July 2022 | Category: Article
© 2024 Novature Tech Pvt Ltd. All Rights Reserved.