




Cloud computing is the use of the Internet to supply IT resources on a pay-as-you-go basis. Instead of purchasing owning, and maintaining physical data centers and servers, we can use a variety of technology services such s computing power, storage, and databases.
Novature Tech is a pioneer in the Penetration testing domain and built a competency center with special focus on Cloud penetration testing and gained over 25+ person months of experience in undertaking projects in Closed penetration testing in the last 1 year.
Benefits of Cloud Penetration Testing
A penetration test is one of the best ways to expose potential vulnerabilities in your system. This can be in relation to a cloud database, an in-house service or any form of tech system you’re operating on.
It all depends on how it is perceived to be. Most business owner feels that cloud space equals cloud security.
How Does Cloud Penetration Testing Differ from Penetration Testing?
Penetration testing, terms is the process of conducting offensive security tests on a system, service or network in order to identify security flaws. So, cloud penetration testing is just a simulation on attack on your cloud services in order to assess their security.
Purpose of Cloud Penetration Testing
The main goal is to identify the security flaws in your cloud service before hackers do. Depending on the type of cloud service and the provider, several manual and automated procedure and tools may be employed.

Penetration Testing Strategies
Targeted penetration testing is conducted by the client’s IT or security team and the testing team working together. Everyone knows what is going on, and no one is taken by surprise. This approach causes a minimum of disruption, since the IT team won’t mistake a test for a real attack. It allows for quick feedback in both directions.
External testing takes the perspective of an outside attacker who (initially) has no system privileges. The testers can see servers and devices which are visible on the Internet. This includes Web, mail, and FTP servers, firewalls, and any devices that may be inadvertently exposed to access. The test includes scanning access points for open ports, probing services, login attempts, and scanning for leaked information.
Internal testing works from a user account given to the tester. The tester determines if the account can take actions or reach resources it shouldn’t be authorized for. Aside from assessing how much harm a rogue employee can do, it measures what can happen if an outsider steals the credentials for an account. In systems that consistently employ the principle of least privilege, a normal account can do only limited harm.
Blind testing is a type of external testing that simulates the actions of an attacker who has picked a target at random. The testers start with very limited information, perhaps just the name of the company or the domain. There aren’t a lot of cases where this type of test is useful. The tester needs to spend additional time gathering information to get to the point of a normal external tester.
Double blind testing is more interesting. Both the tester and the client organization are operating blind. Only a few people on the client side know about the test, and they don’t include IT personnel. To the people in IT, whatever happens is a real attack. This type of test evaluates the ability of IT and security to respond to an intrusion attempt. It carries some risks, since the tech team might quarantine systems or restrict operations in an attempt to stop the “attack.”
Black box testing is similar to blind testing, and the terms are often used interchangeably. Black-box testers know what systems they are targeting but have no knowledge beyond what the public has. This is slightly more information than a true blind tester has, but most often it’s limited to the URL of the company’s website or its IP address. This type of test can help to show if the client has made too much information easily available.
White box testing is also known as clear box testing. The testers get detailed information about the target system, including source code, configurations, and system documentation. It lets testers find the greatest number of weaknesses in the shortest time, and it helps to show what a malicious insider could do. Unlike internal testing, white box testing doesn’t include the credentials for any accounts.
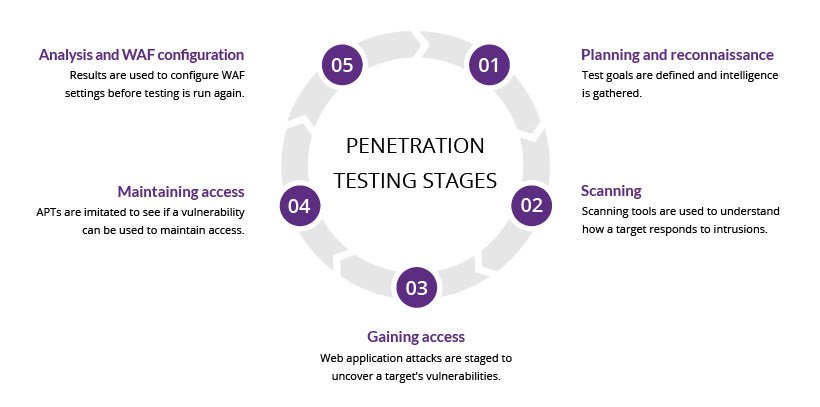
Phases of the Penetration Testing Process
Reconnaissance
The first penetration testing phase is reconnaissance. In this phase, the tester gathers as much information about the target system as they can, including information about the network topology, operating systems and applications, user accounts, and other relevant information. The goal is to gather as much data as possible so that the tester can plan an effective attack strategy.
Reconnaissance can be categorized as either active or passive depending on what methods are used to gather information. Passive reconnaissance pulls information from resources that are already publicly available, whereas active reconnaissance involves directly interacting with the target system to gain information. Typically, both methods are necessary to form a full picture of the target’s vulnerabilities.
Scanning
Once all the relevant data has been gathered in the reconnaissance phase, it’s time to move on to scanning. In this penetration testing phase, the tester uses various tools to identify open ports and check network traffic on the target system. Because open ports are potential entry points for attackers, penetration testers need to identify as many open ports as possible for the next penetration testing phase.
This step can also be performed outside of penetration testing; in those cases, it’s referred to simply as vulnerability scanning and is usually an automated process. However, there are drawbacks to only performing a scan without a full penetration test—namely, scanning can identify a potential threat but cannot determine the level at which hackers can gain access. So, while scanning is essential for cybersecurity, it also needs human intervention in the form of penetration testers to reach its full potential.
Vulnerability Assessment
The third penetration testing phase is vulnerability assessment, in which the tester uses all the data gathered in the reconnaissance and scanning phases to identify potential vulnerabilities and determine whether they can be exploited. Much like scanning, vulnerability assessment is a useful tool on its own but is more powerful when combined with the other penetration testing phases.
When determining the risk of discovered vulnerabilities during this stage, penetration testers have many resources to turn to. One is the National Vulnerability Database (NVD), a repository of vulnerability management data created and maintained by the U.S. government that analyzes the software vulnerabilities published in the Common Vulnerabilities and Exposures (CVE) database. The NVD rates the severity of known vulnerabilities using the Common Vulnerability Scoring System (CVSS).
Exploitation
Once vulnerabilities have been identified, it’s time for exploitation. In this penetration testing phase, the penetration tester attempts to access the target system and exploit the identified vulnerabilities, typically by using a tool like Metasploit to simulate real-world attacks.
This is perhaps the most delicate penetration testing phase because accessing the target system requires bypassing security restrictions. Though system crashes during penetration testing are rare, testers must still be cautious to ensure that the system isn’t compromised or damaged.
Reporting
Once the exploitation phase is complete, the tester prepares a report documenting the penetration test’s findings. The report generated in this final penetration testing phase can be used to fix any vulnerabilities found in the system and improve the organization’s security posture.
Building a penetration testing report requires clearly documenting vulnerabilities and putting them into context so that the organization can remediate its security risks. The most useful reports include sections for a detailed outline of uncovered vulnerabilities (including CVSS scores), a business impact assessment, an explanation of the exploitation phase’s difficulty, a technical risk briefing, remediation advice, and strategic recommendations.
Penetration Testing Tools
There are many different penetration testing tools available, and each has its strengths and weaknesses. Some of the most popular include:
Nmap.
Nmap is a powerful network scanning tool that can scan for open ports and services. It also includes features for identifying vulnerable applications.
Metasploit.
Metasploit is a vulnerability exploitation tool. It includes a library of exploits for a variety of programs and operating systems, as well as a wizard that can assist penetration testers in capitalizing on known vulnerabilities.
Wireshark.
Wireshark is a network analysis tool that can capture packet data from a network and decode it into readable form. This can be useful for identifying malicious traffic or sensitive information being transmitted over a network.
Burp Suite. Burp Suite is an all-in-one web application security testing tool. It can scan websites for vulnerabilities, manipulate requests and responses, and intercept traffic between the client and server.
Author: Thomas A | Posted On: 30th November 2022 | Category: Article
© 2024 Novature Tech Pvt Ltd. All Rights Reserved.